On April 17, 2019, I will be speaking at the MIT Forum about Cybersecurity. This event is open to the public. For details:
Category: My Talks
Giving a talk on Computer Science at CI to the RDP-21 group on Nov 6 at 7:30am
On November 6, 2018, at 7:30am, I am giving a talk to the Regional Defense Partnership for the 21st Century (RDP-21) on Computer Science at CI. Here is the meeting location.
I am giving a talk in Cybersecurity at Point Mugu NAWCWD on October 18
Cybersecurity event @CSUCI on April 20, 2018
On the evening of April 20, 2018 Assemblymember Jacqui Irwin and CSU Channel Islands president Erica D. Beck co-hosted a Cybersecurity event in Sierra Hall, promoting regional industry partnerships. At this event we had the opportunity to showcase our work – three masters students and one senior student presented research under my supervision:
 Zane Gittins spoke about his network penetration testing at HAAS: this work started as a Hank Lacayo Internship at HAAS in the fall of 2017, but since then Zane has been hired by HAAS to continue his work.
Zane Gittins spoke about his network penetration testing at HAAS: this work started as a Hank Lacayo Internship at HAAS in the fall of 2017, but since then Zane has been hired by HAAS to continue his work.
 Eric Gentry spoke about the SEAKER project, a digital forensic tool that was developed with and for the High Technology Task Force (HTTF) at the Ventura forensic lab. We presented this tool at an event on August 7, 2017.
Eric Gentry spoke about the SEAKER project, a digital forensic tool that was developed with and for the High Technology Task Force (HTTF) at the Ventura forensic lab. We presented this tool at an event on August 7, 2017.
 Geetanjali Agarwal spoke about the Image Recognition project, also inspired by the work done at the HTTF at the Ventura lab, where we aim to identify images from partially recovered files and compare them to a bank of images using the difference hash technique.
Geetanjali Agarwal spoke about the Image Recognition project, also inspired by the work done at the HTTF at the Ventura lab, where we aim to identify images from partially recovered files and compare them to a bank of images using the difference hash technique.
 Ryan McIntyre presented his work on algorithms in bio-informatics. These results have been published recently in the Journal of Discrete Algorithms, and described in a blog post on March 6, 2018.
Ryan McIntyre presented his work on algorithms in bio-informatics. These results have been published recently in the Journal of Discrete Algorithms, and described in a blog post on March 6, 2018.
Here are the presentation slides.
I introduced the students making some remarks elaborating on president Beck’s statement about partnerships between CI and the Ventura industry. As a CI faculty, I find interdependence in the triad of Scholarship, Teaching and Industry relations. Many of our projects start by addressing a Research & Development need of the community, such as the SEAKER tool for HTTF. We use it to teach our students a hands-on approach to problem solving in Computer Science; we aim to produce quality work that advances knowledge and is publishable.
Scholarship, the first component of the triad, is really composed of three simultaneous activities: the research itself, which is laborious, time consuming, consisting of literature review and the cycle of hypothesis, testing and proving.
The funding component: labs, equipment, salaries, conferences, all these require funds, which can be secured through grants, philanthropic gifts or state support.
And finally dissemination, which is crucial as without it no one is aware of our work, and which takes place through publishing, conference presentations, blog writing, and events such as the one described in this blog. At CI we are lucky in that Advancement facilitates both fundraising and dissemination.
Thanks to Assemblymember Jaqui Irwin @JacquiIrwin, as well as Professor Michael Soltys @MichaelMSoltys and his Computer Science students for their efforts in addressing Cybersecurity #csuci #camarillo #computerscience #cybersecurity pic.twitter.com/Rhrz85klfj
— Erika D. Beck (@CIPresBeck) April 21, 2018
National Engineers Week Banquet @CSUCI
 It was a great pleasure to Emcee the National Engineers Week of Ventura and Santa Barbara Counties banquet at CSU Channel Islands (CI). This was the 45th annual engineering week dinner, and the second year (in a row) that it took place at CI.
It was a great pleasure to Emcee the National Engineers Week of Ventura and Santa Barbara Counties banquet at CSU Channel Islands (CI). This was the 45th annual engineering week dinner, and the second year (in a row) that it took place at CI.
Thank you to my colleagues Jason Isaacs and Houman Dallali, and their students Adan Sanchez, Alexandra Collette and Nicole Dubin for a display of the student engineering projects at CI. We were delighted to announce that we are welcoming the first cohort of Mechatronics students in the fall of this year (2018). It was especially appropriate to welcome engineers from the local businesses and the local Navy bases at CI, as we pursue three interdependent missions:
- Scholarship
- Teaching
- Engagement in the community
The pièce de résistance event of the evening was a keynote address by Dr. Adam Steltzner, NASA Engineer with Jet Propulsion Laboratory. Dr. Steltzer is a renowned engineer who led the team responsible for the Curiosity Rover’s successful landing on Mars (the EDL: Entry, Descent, Landing system); the famous 7 Minutes of Terror. Last year Dr. Steltzer was named to the National Academy of Engineering.
 It was a great honor to meet Dr. Steltzer and listen to a first hand account of the mission.
It was a great honor to meet Dr. Steltzer and listen to a first hand account of the mission.
Why is it called the 7 Minutes of Terror? In just seven minutes, NASA’s six-wheeled rover called Curiosity, must go from 13,000 mph as it enters the Martian atmosphere to a dead stop on the surface.
During those seven minutes, the rover is on its own. Earth is too far away for radio signals to make it to Mars in time for ground controllers to do anything. Everything in the EDL system must work perfectly, or Curiosity will not so much land as go splat. The team that invented the EDL system, led by Dr. Steltzer, has spent nearly 10 years perfecting it.
Thanks @lex_collette and @nrdubin for showing off our @Swarmathon work at the National Engineers Week dinner @csuci. pic.twitter.com/89h4CWb7E5
— CI.Computer.Science (@csuci_cs) February 24, 2018
Congratulations to @csuci student @sirocknick for winning a National Engineers Week scholarship last night.
— CI.Computer.Science (@csuci_cs) February 24, 2018
Speaking at the Camarillo Chamber of Commerce
President Erika D. Beck speaking at the The Camarillo Chamber of Commerce CI Connection Luncheon pic.twitter.com/U71BPZMvH0
— CSU Channel Islands (@csuci) February 15, 2018
my remarks
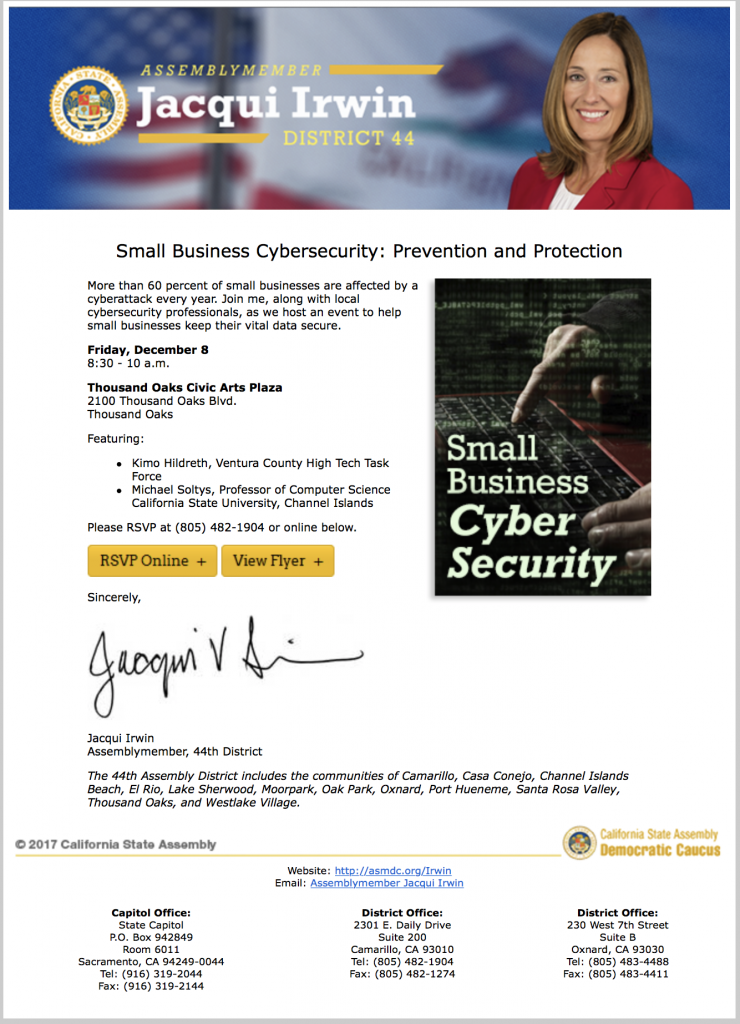
I will be giving a talk on Cybersecurity for small businesses on December 8
Detective Kimo Hildreth and I will be giving a talk at a breakfast event on Cybersecurity for Small Businesses on Friday December 8, 2017, at 8:30am. To RSVP and view more event details click here. The event is organized by Assemblymember Jacqui Irwin, and it will take place at 2100 Thousand Oaks Blvd, in the “Oak and Park Room”.
OLLI talk on Cybersecurity June 8 at 10:00am
Michael Soltys OLLI talk on Cybersecurity
June 8, 10:00am-12:00pm.
In Broome Library 2325
Title: Best practices for staying safe on the Internet
Abstract: The Internet enables us to do wonderful things: stay connected with family and friends (e.g., Skype), shop from the comfort of our home (e.g., Amazon), watch movies at the time of our choosing and without commercials (e.g., Netflix), and check news headlines personalized to our interests and tastes (e.g., Twitter). But all this comes with a slew of threats and dangers: like the highwaymen of old, hackers prey on vulnerable victims, without having to leave their house, and covered by a blanket of anonymity. This talk will present best practices to stay safe on the Internet, enjoy its benefits, and reduce its risks.
CI press release re my forthcoming SAME talk on cybersecurity
CSUCI Cyber-security expert to speak at on-campus engineering convention.
 Camarillo, Calif., Feb. 20, 2017—Whether it’s personal information, medical records, national security or election results, computer hacking is a rising national and global concern.
Camarillo, Calif., Feb. 20, 2017—Whether it’s personal information, medical records, national security or election results, computer hacking is a rising national and global concern.
CSU Channel Islands (CSUCI) Computer Science Chair and Professor Michael Soltys, Ph.D., will share his cybersecurity expertise to an audience of professional engineers from 11 a.m. to 2 p.m. on March 23 in the Grand Salon.
“Our society is under constant cyber-threat, as our infrastructure, our economy, and our privacy, depend on secure IT systems,” Soltys said. “My talk will consider the major threats, and present examples of how hackers attack our systems.”
Sponsored by the nonprofit Oxnard Ventura Post of the Society of American Military Engineers, the presentation is geared toward an audience with a high degree of computer expertise, so Soltys plans to share cybersecurity best practices.
“I plan to give more of a technical talk from the engineering point of view,” Soltys said. “How to write code that is more defended. I plan to show techniques hackers use to get into systems.”
One of the principal causes of cyber-vulnerability is faulty software, a problem Soltys addresses in a textbook on algorithms he wrote for software engineers.
Aside from his teaching at CSUCI, Soltys also acts as Director of IT Security for Executek International where he specializes in forensic work.
The public is welcome at the presentation, which is on campus at One University Drive in Camarillo. Cost is $30 a person for lunch.
Follow the directional signage to Parking Lots A-4 and A-11, then follow “walk this way” signage to the Grand Salon.
To register for the presentation, click on:
http://www.same.org/Oxnard-Ventura
Talk at PSC2016 on paper with Neerja Mhaskar
 I just gave a talk at PSC2016 conference in Prague based on a paper with Neerja Mhaskar, Forced repetitions over alphabet lists. This paper explores further the problem posed by Grytczuk in 2010 regarding the construction of non-repetitive strings over alphabet lists where each alphabet has 3 symbols. We use some string combinatorics, as well as an approach based on the Crossing sequences technique from complexity theory. The conference took place at České vysoké učeni technické v Praze – Fakulta stavebni, which is quite a mouthful to say, even for a fellow slav :), and is the Czech Technical University in Prague.
I just gave a talk at PSC2016 conference in Prague based on a paper with Neerja Mhaskar, Forced repetitions over alphabet lists. This paper explores further the problem posed by Grytczuk in 2010 regarding the construction of non-repetitive strings over alphabet lists where each alphabet has 3 symbols. We use some string combinatorics, as well as an approach based on the Crossing sequences technique from complexity theory. The conference took place at České vysoké učeni technické v Praze – Fakulta stavebni, which is quite a mouthful to say, even for a fellow slav :), and is the Czech Technical University in Prague.
Slides are attached:
[slideshare id=65540986&doc=soltys-psc2016-slides-160831083913]
Some other pictures: