Zane Gittins is a Systems Security Engineer at Haas Automation and recently graduated from CSUCI with a bachelors in Computer Science. Zane started his journey at Haas as an intern through CSUCI partnerships with local business and was recently hired full time. During his undergraduate career he worked under Dr. Pilarcyzk as an assistant in research focused on Persistent Homology. During his capstone project he worked closely with Dr. Soltys to provide a security best practices document to Haas. He continues to expand his education in the CI masters of Computer Science program (MSCS).
Zane Gittins is a Systems Security Engineer at Haas Automation and recently graduated from CSUCI with a bachelors in Computer Science. Zane started his journey at Haas as an intern through CSUCI partnerships with local business and was recently hired full time. During his undergraduate career he worked under Dr. Pilarcyzk as an assistant in research focused on Persistent Homology. During his capstone project he worked closely with Dr. Soltys to provide a security best practices document to Haas. He continues to expand his education in the CI masters of Computer Science program (MSCS).
Tag: Cybersecurity
Understanding Cybersecurity & Privacy Best Practices

Source: (18) Understanding Cybersecurity & Privacy Best Practices | LinkedIn
Decade of research shows little improvement in password guidance
Leading internet brands including Amazon and Wikipedia are failing to support users with advice on how to securely protect their data, a study shows.More than a decade after first examining the issue, research by the University of Plymouth has shown most of the top ten English-speaking websites offer little or no advice guidance on creating passwords that are less likely to be hacked.Some still allow people to use the word ‘password’, while others will allow single-character passwords and basic words including a person’s surname or a repeat of their user identity.
Source: Decade of research shows little improvement in password guidance – University of Plymouth
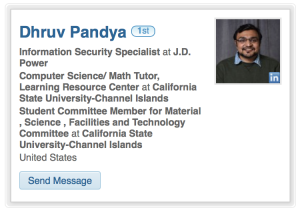
Congratulations Dhruv Pandya
Congratulations Dhruv Pandya, an alum of the MSCS program at CI, for a new position as an Information Security Specialist at J.D. Power.
Cyber Quest Competition
This Cyber Security event might be of interest to your students
Carlos Miranda
Associate Director of Information Security
CSU Channel Islands
One University Drive, Camarillo, CA 93012
U.S. Cyber Challenge’s annual online competition, Cyber Quests, is now open to competitors! But, hurry and register at www.CyberQuests.org as the last day to register is Monday, April 30, 2018.
This year’s focus is on cryptography and everyone is welcome to participate –whether you are a student or professional; novice or highly-experienced; a US citizen or international, all are welcome! You have 3 chances to earn a top score & top performers who are US citizens and 18+ years old will be invited to attend one of U.S. Cyber Challenge’s week-long cyber camps this summer for intensive training & a CTF competition.
Cybersecurity event @CSUCI on April 20, 2018
On the evening of April 20, 2018 Assemblymember Jacqui Irwin and CSU Channel Islands president Erica D. Beck co-hosted a Cybersecurity event in Sierra Hall, promoting regional industry partnerships. At this event we had the opportunity to showcase our work – three masters students and one senior student presented research under my supervision:
 Zane Gittins spoke about his network penetration testing at HAAS: this work started as a Hank Lacayo Internship at HAAS in the fall of 2017, but since then Zane has been hired by HAAS to continue his work.
Zane Gittins spoke about his network penetration testing at HAAS: this work started as a Hank Lacayo Internship at HAAS in the fall of 2017, but since then Zane has been hired by HAAS to continue his work.
 Eric Gentry spoke about the SEAKER project, a digital forensic tool that was developed with and for the High Technology Task Force (HTTF) at the Ventura forensic lab. We presented this tool at an event on August 7, 2017.
Eric Gentry spoke about the SEAKER project, a digital forensic tool that was developed with and for the High Technology Task Force (HTTF) at the Ventura forensic lab. We presented this tool at an event on August 7, 2017.
 Geetanjali Agarwal spoke about the Image Recognition project, also inspired by the work done at the HTTF at the Ventura lab, where we aim to identify images from partially recovered files and compare them to a bank of images using the difference hash technique.
Geetanjali Agarwal spoke about the Image Recognition project, also inspired by the work done at the HTTF at the Ventura lab, where we aim to identify images from partially recovered files and compare them to a bank of images using the difference hash technique.
 Ryan McIntyre presented his work on algorithms in bio-informatics. These results have been published recently in the Journal of Discrete Algorithms, and described in a blog post on March 6, 2018.
Ryan McIntyre presented his work on algorithms in bio-informatics. These results have been published recently in the Journal of Discrete Algorithms, and described in a blog post on March 6, 2018.
Here are the presentation slides.
I introduced the students making some remarks elaborating on president Beck’s statement about partnerships between CI and the Ventura industry. As a CI faculty, I find interdependence in the triad of Scholarship, Teaching and Industry relations. Many of our projects start by addressing a Research & Development need of the community, such as the SEAKER tool for HTTF. We use it to teach our students a hands-on approach to problem solving in Computer Science; we aim to produce quality work that advances knowledge and is publishable.
Scholarship, the first component of the triad, is really composed of three simultaneous activities: the research itself, which is laborious, time consuming, consisting of literature review and the cycle of hypothesis, testing and proving.
The funding component: labs, equipment, salaries, conferences, all these require funds, which can be secured through grants, philanthropic gifts or state support.
And finally dissemination, which is crucial as without it no one is aware of our work, and which takes place through publishing, conference presentations, blog writing, and events such as the one described in this blog. At CI we are lucky in that Advancement facilitates both fundraising and dissemination.
Thanks to Assemblymember Jaqui Irwin @JacquiIrwin, as well as Professor Michael Soltys @MichaelMSoltys and his Computer Science students for their efforts in addressing Cybersecurity #csuci #camarillo #computerscience #cybersecurity pic.twitter.com/Rhrz85klfj
— Erika D. Beck (@CIPresBeck) April 21, 2018
Speaking at the Camarillo Chamber of Commerce
President Erika D. Beck speaking at the The Camarillo Chamber of Commerce CI Connection Luncheon pic.twitter.com/U71BPZMvH0
— CSU Channel Islands (@csuci) February 15, 2018
my remarks
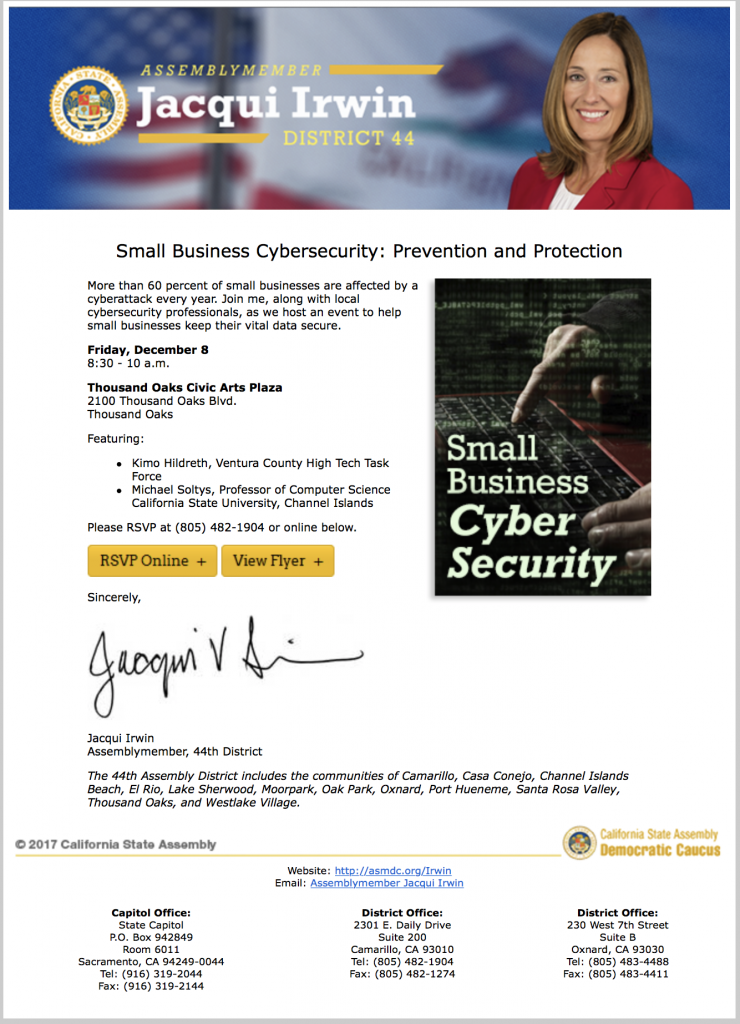
I will be giving a talk on Cybersecurity for small businesses on December 8
Detective Kimo Hildreth and I will be giving a talk at a breakfast event on Cybersecurity for Small Businesses on Friday December 8, 2017, at 8:30am. To RSVP and view more event details click here. The event is organized by Assemblymember Jacqui Irwin, and it will take place at 2100 Thousand Oaks Blvd, in the “Oak and Park Room”.
msoltys-talk-dec8-2017CI Computer Science students build a digital forensic tool
 On August 7, 2017, the CI Computer Science students presented a prototype of a digital forensic tool, which we named SEAKER (Storage Evaluator and Knowledge Extraction Reader), as part of their Masters COMP 524 Cybersecurity course. This project was a collaboration between the Ventura County District Attorney (VCDA) Digital Forensics Lab and CI Computer Science, under the umbrella of the SoCal High Technology Task Force (HTTF).
On August 7, 2017, the CI Computer Science students presented a prototype of a digital forensic tool, which we named SEAKER (Storage Evaluator and Knowledge Extraction Reader), as part of their Masters COMP 524 Cybersecurity course. This project was a collaboration between the Ventura County District Attorney (VCDA) Digital Forensics Lab and CI Computer Science, under the umbrella of the SoCal High Technology Task Force (HTTF).
The students presented a live demo with devices supplied by the Ventura County DA. The SEAKER prototype was able to compile search results in less than a minute depending on the size of the device. According to VCDA officials at the presentation this is a remarkable increase in efficiency and will be a useful tool in the field: while imaging of a hd can take up to 4 hours, SEAKER performs a triage search in minutes.
Digital Forensics (DF) deals with the recovery and investigation of clues from digital devices (computers, handhelds, iPads, routers, modems, DVRs, etc.). The goal of this effort is to support or refute a hypothesis in court. DF is a complex and technical field: it can be used to attribute evidence to specific suspects, confirm alibis or statements, determine intent, identify sources, or authenticate documents.
A DF investigation commonly consists of 3 stages: acquisition or imaging of exhibits, analysis and reporting. The SEAKER tool helps with the acquisition of data from digital devices in a way that prevents tampering.
 The SEAKER project was a fantastic learning experience for our students, as its design and prototyping combined many different skills: The C programming language, BASH shell scripting, the Linux Operating Systems and command line, the Raspberry Pi hardware, Gliffy diagrams, Dropbox Paper (which we used as a Wiki); Slack collaborative discussion / brainstorming tool, the GitHub software repository which was used as a collaborative tool in the design of the software that animated the Raspberry Pi, WordPress blogging, AWS S3 which served as a repository of the final product, Grep (regular expressions and pattern matching), working with different file systems, and of course strict performance (speed, read only). All of this had to be combined by a group of 18 students, with different backgrounds and skill sets to produce something that could be used by DF examiners.
The SEAKER project was a fantastic learning experience for our students, as its design and prototyping combined many different skills: The C programming language, BASH shell scripting, the Linux Operating Systems and command line, the Raspberry Pi hardware, Gliffy diagrams, Dropbox Paper (which we used as a Wiki); Slack collaborative discussion / brainstorming tool, the GitHub software repository which was used as a collaborative tool in the design of the software that animated the Raspberry Pi, WordPress blogging, AWS S3 which served as a repository of the final product, Grep (regular expressions and pattern matching), working with different file systems, and of course strict performance (speed, read only). All of this had to be combined by a group of 18 students, with different backgrounds and skill sets to produce something that could be used by DF examiners.
 One of the CI pillars is Community Engagement and Service Learning. This approach identifies needs in the community, and builds a curriculum around research and development to address those needs. The SEAKER project is a great example of such a symbiotic relation between CI and the community. Also, it is an example of the strength of a pedagogical approach that combines both theory and practice. Without theory a field becomes a collection of ad hoc procedures. But without practice theory becomes an abstract exercise in intellectual virtuosity. We plan to build on the approach that combines the Service Learning and Theory & Practice paradigms as we go forward with our Computer Science program in Security Systems Engineering and our Masters level offering in Cybersecurity.
One of the CI pillars is Community Engagement and Service Learning. This approach identifies needs in the community, and builds a curriculum around research and development to address those needs. The SEAKER project is a great example of such a symbiotic relation between CI and the community. Also, it is an example of the strength of a pedagogical approach that combines both theory and practice. Without theory a field becomes a collection of ad hoc procedures. But without practice theory becomes an abstract exercise in intellectual virtuosity. We plan to build on the approach that combines the Service Learning and Theory & Practice paradigms as we go forward with our Computer Science program in Security Systems Engineering and our Masters level offering in Cybersecurity.
Some photos from the event:
SEAKER presentation at CI on August 7 at 6pm in DEL NORTE 1530
seaker
“Storage Evaluator And Knowledge Extraction Reader”

On Monday August 7, at 6pm, in DEL NORTE 1530, the COMP 524 (Cybersecurity) students will present their final project, a technical solution for the SoCal High Technology Task Force in Ventura. This project implements a digital forensic tool with strict performance requirements.
We used GitHub as the software repository, Dropbox Paper for the documentation Wiki, and AWS S3 for distribution of the production version of the software.
You are cordially invited to attend; the presentation will take about two hours, and there will be snacks (Short link to this post: https://wp.me/p7D4ee-FJ).