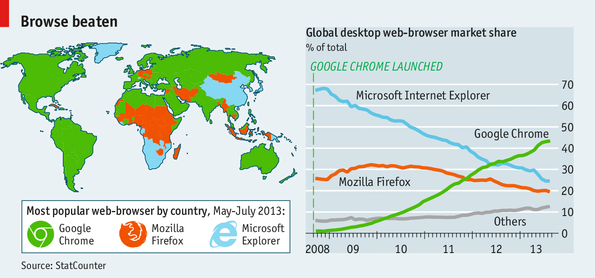
A number of postdoc positions are currently available at CTIC, Department of Computer Science. The positions are for 1 year with the possibility of extension. The intended starting date is 1 August 2014. We are looking for applicants committed to playing an active part in continuously building strong research collaborations between the Department of Computer Science at Aarhus University (www.cs.au.dk) and IIIS at Tsinghua University, Beijing. In particular, the successful applicants will spend significant time at IIIS, with funding for such visits being part of the post doc position.
via CTIC.