Blog
Two 1-year research positions are available at the Department of Computer Science of the University of Pisa
Two 1-year research positions are available at the Department of Computer Science of the University of Pisa.
The positions are funded on the Project MIUR-SIR (2014) CMACBioSeq. The aim of this project is to develop research in the area of Data Compression and Sequence Analysis by using methods from Combinatorics on Words and by developing algorithms and data structures for the treatment of strings (indexing, querying, analyzing, …), mainly datasets from Next-generation Sequencing (NGS) technologies or third generation sequencing technologies.
Candidates with expertise in string/parallel algorithms and NGS bioinformatics are encouraged to apply.
Research areas include:
– string algorithmics,
– text indexing for big data,
– indexes for approximate pattern matching
– text compression and compressed text indexing,
– external memory indexes,
– space efficient data structures,
– shared memory parallel computing,
– and so on.
* Application deadline: May 2017, 27th
* Start date : June 2017 (negotiable)
* Duration: 12 months
* Expected: Master’s Degree (or PhD).
For detailed job descriptions and how to apply, visit:
https://www.unipi.it/ateneo/bandi/assegni/2017/inf/27mag2017/inglese.rtf_pdfcvt.pdf
https://www.unipi.it/ateneo/bandi/assegni/2017/inf/27mag2017/index.htm
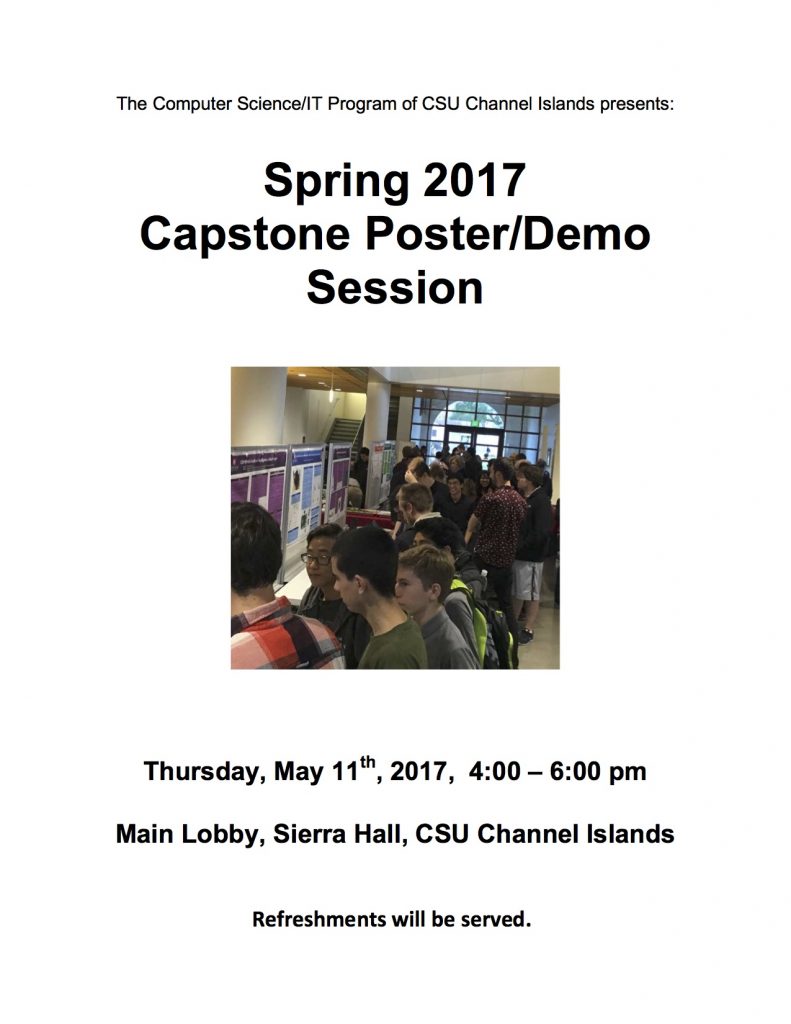
CS @CSUCI Capstone Showcase Thursday May 11 4-6pm in Sierra hall lobby
CI Begins Preparing For Proposed Engineering Program
 A university on the South Coast is preparing for a new engineering program it hopes to have in place within the next two years.Cal State Channel Islands in Camarillo proposed to launch an engineering program last summer. University officials say they’re still awaiting final approval from the CSU Chancellor’s Office, but they expect to get a green light soon.
A university on the South Coast is preparing for a new engineering program it hopes to have in place within the next two years.Cal State Channel Islands in Camarillo proposed to launch an engineering program last summer. University officials say they’re still awaiting final approval from the CSU Chancellor’s Office, but they expect to get a green light soon.
So, they’ve begun the planning process for a program focused on mechatronics, which is a combination of mechanical and electrical engineering.
“The animation of mechanical devices by software” said Michael Soltys, chair of the Computer Science Department, which mechatronics will be housed under.
He said few engineering programs have an emphasis in this field.“We’re thinking of starting mechatronics with small robotic mobility, like drones, like underwater robots. Robots that move, that walk, that drive,” he said.
The university has begun hiring faculty and designing courses. The goal is to start the engineering program in the fall of 2018 with 24 students.
Source: South Coast University Begins Preparing For Proposed Engineering Program | KCLU
Mechatronics at CI
The following from: https://www.kclu.org/post/south-coast-university-begins-preparing-proposed-engineering-program#stream/0
A university on the South Coast is preparing for a new engineering program it hopes to have in place within the next two years.
Cal State Channel Islands in Camarillo proposed to launch an engineering program last summer. University officials say they’re still awaiting final approval from the CSU Chancellor’s Office, but they expect to get a green light soon.
So, they’ve begun the planning process for a program focused on mechatronics, which is a combination of mechanical and electrical engineering.
“The animation of mechanical devices by software” said Michael Soltys, chair of the Computer Science Department, which mechatronics will be housed under.
He said few engineering programs have an emphasis in this field.
“We’re thinking of starting mechatronics with small robotic mobility, like drones, like underwater robots. Robots that move, that walk, that drive,” he said.
The university has begun hiring faculty and designing courses. The goal is to start the engineering program in the fall of 2018 with 24 students.
CS @CSUCI talk in Mechatronics May 9 at 6pm in SIE 1411 by Houman Dallali
Why You Really Need to Stop Using Public Wi-Fi
 In today’har busy world, convenience seems to outweigh consequence, especially with how people use their mobile devices. Using free public Wi-Fi networks, for example, comes with any number of serious security risks, yet surveys show that the overwhelming majority of Americans do it anyway. In a study by privatewifi.com, a whopping three-quarters of people admitted to connecting to their personal email while on public Wi-Fi.
In today’har busy world, convenience seems to outweigh consequence, especially with how people use their mobile devices. Using free public Wi-Fi networks, for example, comes with any number of serious security risks, yet surveys show that the overwhelming majority of Americans do it anyway. In a study by privatewifi.com, a whopping three-quarters of people admitted to connecting to their personal email while on public Wi-Fi.
It isn’t hard to see that a few moments of online convenience are far outweighed by your money or financial information being stolen, or by suffering the embarrassment of your personal information being publicly released. According to a recent opinion poll, more people are leery of public Wi-Fi networks than of public toilet seats (a promising sign). But an interesting experiment, conducted at the 2016 Republican and Democratic National Conventions, showed attendees’ true colors. At each convention, private entities provided visitors with free public Wi-Fi networks (for social science purposes). Around 70% of people connected to the nonsecure Wi-Fi networks at both conferences.
There are dozens of online tutorials showing hackers how to compromise public Wi-Fi, some of them with millions of views. The most common method of attack is known as “Man in the Middle.” In this simple technique, traffic is intercepted between a user’s device and the destination by making the victim’s device think the hacker’s machine is the access point to the internet. A similar, albeit more sinister, method is called the “Evil Twin.” Here’s how it works: You log on to the free Wi-Fi in your hotel room, thinking you’re joining the hotel’s network. But somewhere nearby, a hacker is boosting a stronger Wi-Fi signal off of their laptop, tricking you into using it by labeling it with the hotel’s name. Trying to save a few bucks, and recognizing the name of the hotel, you innocently connect to the hacker’s network. As you surf the web or do your online banking, all your activity is being monitored by this stranger.Still not convinced of the risks? Here’s a story that should worry business travelers in particular. In 2014 experts from Kaspersky Lab uncovered a very sophisticated hacking campaign called “Dark Hotel.” Operating for more than seven years and believed to be a sophisticated economic espionage campaign by an unknown country, Dark Hotel targeted CEOs, government agencies, U.S. executives, NGOs, and other high-value targets while they were in Asia. When executives connected to their luxury hotel’s Wi-Fi network and downloaded what they believed were regular software updates, their devices were infected with malware. This malware could sit inactive and undetected for several months before being remotely accessed to obtain sensitive information on the device.
What is the best way to protect yourself against these kinds of Wi-Fi threats? Although antivirus protection and firewalls are essential methods of cyber defense, they are useless against hackers on unsecured Wi-Fi networks. Consider the following seven security tips to keep prying eyes out of your devices:
- Don’t use public Wi-Fi to shop online, log in to your financial institution, or access other sensitive sites — ever
- Use a Virtual Private Network, or VPN, to create a network-within-a-network, keeping everything you do encrypted
- Implement two-factor authentication when logging into sensitive sites, so even if malicious individuals have the passwords to your bank, social media, or email, they won’t be able to log in
- Only visit websites with HTTPS encryption when in public places, as opposed to lesser-protected HTTP addresses
- Turn off the automatic Wi-Fi connectivity feature on your phone, so it won’t automatically seek out hotspots
- Monitor your Bluetooth connection when in public places to ensure others are not intercepting your transfer of data
- Buy an unlimited data plan for your device and stop using public Wi-Fi altogether
Google Shuts Down Docs Phishing Spree
Google said it has disabled offending accounts involved in a widespread spree of phishing emails today impersonating Google Docs.The emails, at the outset, targeted journalists primarily and attempted to trick victims into granting the malicious application permission to access the user’s Google account. It’s unknown how many accounts were compromised, or whether other applications are also involved. Google advises caution in clicking on links in emails sharing Google Docs.
The messages purport to be from a contact, including contacts known to the victim, wanting to share a Google Doc file. Once the “Open in Docs” button is clicked, the victim is redirected to Google’s OAUTH2 service and the user is prompted to allow the attacker’s malicious application, called “Google Docs,” below, to access their Google account and related services, including contacts, Gmail, Docs and more.
Source: Google Shuts Down Docs Phishing Spree | Threatpost | The first stop for security news
Meet the Hackers Holding Netflix to Ransom – Motherboard
The Dark Overlord attempted to extort plenty of companies before targeting Netflix.
Last week, a hacker or group of hackers dumped apparent full episodes of Orange Is the New Black after Netflix allegedly declined to pay a ransom, and has threatened to release a number of other shows too, including Celebrity Apprentice, New Girl, and The Catch. But this was only the latest move from the group. Known as The Dark Overlord, the hackers have established themselves with a dizzying number of data breaches, often stealing mountains of sensitive corporate and personal data.
For nearly a year, Motherboard and a handful of other journalists have followed The Dark Overlord, and watched it evolve from a group learning how to manipulate the media to aid in extortion attempts, to a ruthless and apparently organized criminal enterprise, albeit one whose ultimate financial success is unclear.
Source: Meet the Hackers Holding Netflix to Ransom – Motherboard
OLLI talk on Cybersecurity June 8 at 10:00am
Michael Soltys OLLI talk on Cybersecurity
June 8, 10:00am-12:00pm.
In Broome Library 2325
Title: Best practices for staying safe on the Internet
Abstract: The Internet enables us to do wonderful things: stay connected with family and friends (e.g., Skype), shop from the comfort of our home (e.g., Amazon), watch movies at the time of our choosing and without commercials (e.g., Netflix), and check news headlines personalized to our interests and tastes (e.g., Twitter). But all this comes with a slew of threats and dangers: like the highwaymen of old, hackers prey on vulnerable victims, without having to leave their house, and covered by a blanket of anonymity. This talk will present best practices to stay safe on the Internet, enjoy its benefits, and reduce its risks.