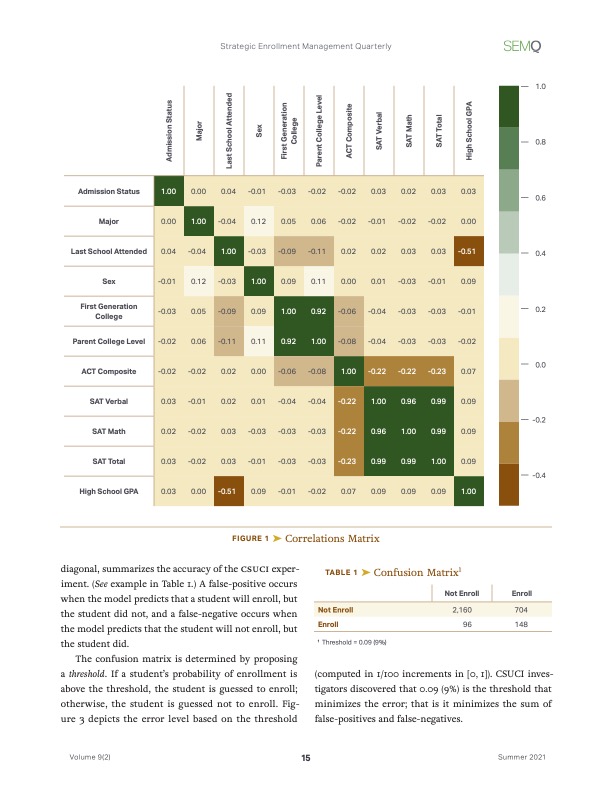
Tech and STEM-related jobs offer the best opportunity for jobhunters and career-switchers to find satisfaction in their work, according to new careers data from Glassdoor.
Glassdoor’s 25 Best Jobs List for 2022 found that software developers, data scientists, IT architects and full-stack engineers dominate the top spots when measured by salary, job satisfaction and the number of job openings.
These three factors were taken from ratings from “hundreds of thousands” of employee reviews on the Glassdoor platform, which were combined with the number of role vacancies to create an overall ‘job score’.
Source: This tech job has just been crowned the best in the country | ZDNet