an information talk
Click here.
overview
 The Department of Computer Science at CSU Channel Islands is delighted to announce that we will be starting a new program in Mechatronics Engineering in 2018.
The Department of Computer Science at CSU Channel Islands is delighted to announce that we will be starting a new program in Mechatronics Engineering in 2018.
We will be taking in the first group of 24 students in the fall of 2018, and growing the program by a new cohort of 24 students every year after that, for a total of just under 100 students thereafter.
CSUCI’s news release and landing page:
In the local news:
Alternative (short) links to this page:
The CI Mechatronics program has been assigned, by the Chancellor’s Office, the following:
- CSU degree-program code:
09102
- CIP code:
14.4201
Mechatronics Zoom meeting on Tuesday, Nov. 7 at 6:00 p.m.; to register
Mechatronics Flyer:
What is Mechatronics?
Mechatronics is a fast growing area of Engineering that is interdisciplinary by nature, as it combines aspects of Mechanics, Control Theory, Computer Science, and Electronics, in order to improve and optimize the design and functionality of systems, as well as making them more economical and reliable. Industrial robots and drones are quintessential examples of mechatronics systems: they include aspects of electronics, mechanics, and computing. Modern production equipment consists of mechatronic modules that are integrated according to a suitable control architecture. Popular examples include automotive subsystems, including anti-lock brakes and spin-assist, as well as everyday equipment, such as autofocus cameras, video, hard disks and CD players.
The complexity of mechatronics requires at least a bachelor’s degree to get into the field. Although the U.S. Bureau of Labor Statistics (BLS) does not provide specific salary information for mechatronics engineers, it does show that median annual wages for all specialized engineers not categorized was $92,680 as of May 2013. The middle 50% of these professionals earned between $68,610 and $117,930 yearly.
The need for mechatronics at ci
CSU Channel Islands is the only public university in the County of Ventura. The campus is strategically located on the so called “101 Tech Corridor,” sharing the neighborhood with companies such as Amgen, Haas, Teledyne Technologies, HRL Laboratories, and many others, not to mention Point Mugu and Port Hueneme Naval bases, as well as Lockheed, Rocketdyne, and other companies in the greater Los Angeles area. Therefore there is a great need and demand for engineers in the local industry and community.
The local companies strongly support the establishment of an Engineering program on the CI campus, and a comprehensive report was produced in 2013 with recommendation for an engineering degree that would meet the needs of the community. In this report it was noted that Ventura County hires about 290 engineers each year, not to mention that the local Naval Bases send their officers to complete their Engineering degrees across the nation, which results in high costs for the Navy, and a loss of revenue for Ventura County.
Mechatronics curriculum
Note that this is still a provisional curriculum; we may make small changes to it as we are implementing the program for the start date of fall 2018.
| Code |
Name |
Units |
GE |
Prerequisites in Place |
| CHEM 105 |
Introduction to Chemistry |
3 |
|
No prerequisites |
| MATH 150 |
Calculus I |
4 |
3 |
Calculus Placement Exam. or MATH 105 |
| EMEC 121 |
Programming in C part 1 |
4 |
3 |
MATH 105 or equiv., COMP 105 or permission |
| EMEC 122 |
Programming in C part 2 |
4 |
|
EMEC 121 |
| MATH 250 |
Calculus III |
3 |
|
MATH 151 with at least a C |
| COMP 151 |
Data Structures and Program Design |
4 |
|
COMP 150 |
| COMP 162 |
Computer Architecture and Assembly Language |
3 |
|
COMP 150 |
| MATH/PHIL 230 |
Logic and Mathematical Reasoning |
3 |
3 |
No prerequisites |
| MATH 240 |
Linear Algebra |
3 |
|
MATH 151 |
| COMP 232 |
Programming Languages |
3 |
|
COMP 150, COMP 151, COMP 162 |
| COMP 262 |
Computer Organization and Architecture |
3 |
|
COMP 151, COMP 162 |
| EMEC 200 |
Logic Circuits |
4 |
|
MATH 150, MATH 230, COMP 162 |
| EMEC 225 |
Engineering Design |
3 |
|
EMEC 200 |
| PHYS 200 |
General Physics I |
4 |
3 |
MATH 150 |
| PHYS 201 |
General Physics II |
4 |
|
PHYS 200, MATH 151 |
| EMEC/PHYS 221 |
Engineering Materials |
3 |
|
CHEM 105, PHYS 200 |
| PHYS 301 |
Classical Mechanics |
3 |
|
PHYS 200, MATH 350 |
| COMP 350 |
Introduction to Software Engineering |
3 |
|
COMP 232, COMP 262 |
| MATH 350 |
Differential Equations & Dynamical Systems |
3 |
|
MATH 250 |
| MATH 352 |
Probability and Statistics |
3 |
|
MATH 351 |
| EMEC/PHYS 310 |
Electronics |
4 |
|
PHYS 201 |
| EMEC 311 |
Digital Systems Design |
3 |
|
EMEC 200 |
| EMEC 315 |
Modeling of Mechatronics Systems |
3 |
|
MATH 350 |
| EMEC 316 |
Sensors and Measurements |
3 |
|
COMP 151, EMEC/PHYS 310 |
| EMEC/COMP 462 |
Embedded Systems |
3 |
|
COMP 350 or consent |
| EMEC/COMP 470 |
Mobile Robotics |
3 |
|
COMP 350, MATH 240 or consent |
| EMEC 463 |
Feedback Control Systems |
3 |
|
MATH 240, MATH 350 |
| EMEC 491 |
Capstone Preparation |
1 |
|
Senior standing in Mechatronics Major |
| EMEC 499 |
Capstone |
3 |
|
Senior standing in Mechatronics Major |
|
Major |
93 |
|
|
|
GE/AIR |
39 |
|
|
|
Total |
132 |
|
|
| Optional Electives: |
| EMEC 401 |
Fluid Mechanics |
3 |
|
Senior standing in Mechatronics Major |
| EMEC/PHYS 305 |
Thermal and Statistical Physics |
3 |
|
MATH 350, PHYS 201 |
| COMP/ART/IT 464 |
Computer Graphic System and Design I |
3 |
|
COMP 350, MATH 240 |
student learning outcomes
We envision the following Program Learning Outcomes; our graduates will:
- Be competent engineers and problem solvers.
- Possess a high level of erudition in the field of Mechatronics Engineering.
- Have knowledge of standard engineering tools, and their application in the field.
- Be effective communicators.
- Be prepared to undertake engineering jobs in a wide variety of engineering fields.
Based on our experience, and the experience of other programs, we propose the following initial small set of Student Learning Outcomes:
- Apply knowledge of Mathematics, Science, and Engineering.
- Design experiments to evaluate the performance of a mechatronic system or component with respect to specifications.
- Design a mechatronic system, component, or process to meet desired needs.
- Define and solve an Engineering problem.
- Develop and defend a written statement of professional ethical responsibility related to their field of study.
- Ability to communicate effectively.
1 will be covered in the first two years’ science and introductory courses (programming, calculus, chemistry, physics, etc.), and rigorous logical / critical thinking will be taught in many courses, for example MATH/PHIL 230. 2, 3, 4 will be covered in multiple courses, for example Engineering Design will be taught in EMEC 225, while solving engineering problems will be taught in Mobile Robotics (EMEC/COMP 470) or Embedded Systems (EMEC/COMP 462). Communication skills will be taught in General Education courses, such as first-year writing courses.
summary of new courses
EMEC 200 – Logic Circuits: Basics of digital electronic devices and methodologies used in digital circuit design. Design, analysis and trouble shooting of logic gates, counters, registers, memory units, pulse and switching circuits, and control circuits. Comparison of digital TTL integrated circuits with other families of logic devices. Includes student projects.
EMEC/PHYS 221 – Engineering Materials: Examines the interrelationships between processing, structure, properties, and performance of various engineering materials such as metals, polymers, ceramics, composites, and semiconductors. Studies the effects of heat, stress, imperfections, and chemical environments upon material properties and performance. Emphasizes developing an ability to select appropriate materials to meet engineering design criteria.
EMEC 225 – Engineering Design: Introduction to engineering design processes, methods, and decision making using team design projects; design communication methods including graphical, verbal, and written.
EMEC 311 – Digital Systems Design: Introduces students to the design of digital systems using hardware description languages. The student will the use computer-aided design tools to design, simulate, prototype, and verify complex digital systems using programmable logic devices and field-programmable gate arrays.
EMEC 315 – Modeling of Mechatronic Systems: Introduces students to modeling techniques and analysis of mechatronic systems. Topics such as state-space and transfer function representation, linearization, and frequency domain analysis are covered. Simulation software will be utilized to quantify and visualize system performance.
EMEC 316 – Sensors and Measurements: Basic measurements with standard laboratory instruments and common sensor interfaces are introduced. Topics include the calibration, transient responses, and statistical characterization of common sensors used in mechatronic systems.
EMEC 401 – Fluid Mechanics: Principal concepts and methods of fluid mechanics are introduced. Students will learn to apply these concepts and methods to the design of fluid systems.
EMEC 463 – Feedback Control Systems: Analysis and design of feedback control systems. Topics include representing dynamical systems with transfer functions and state variables, stability and dynamic analysis using techniques from both the time and frequency domains, the design of feedback regulators and controllers, and computer aided design and analysis.
EMEC 491 – Capstone Preparation: Research and develop a proposal for a significant Mechatronics project under faculty supervision.
EMEC 499 – Capstone: Design, implement and present a significant Mechatronics project under faculty supervision.
abet accreditation
From the ABET website:
We are a nonprofit, non-governmental accrediting agency for programs in applied science, computing, engineering and engineering technology and we are recognized as an accreditor by the Council for Higher Education Accreditation.
ABET accreditation provides assurance that a college or university program meets the quality standards of the profession for which that program prepares graduates.
A scrutiny of the ABET requirements for Mechatronics shows that many of the courses required for such a degree are already being offered at CI. We have a strong offering in Computer Science, Mathematics, and Physics, and with a modicum of effort we could have a program meeting the requirements for an ABET accreditation. The main investment would be three new faculty members, and appropriate lab equipment. We have already hired a new faculty (starting date fall 2017), Houman Dallali, and we are going to hire further two new faculty. Our goal is to seek ABET accreditation within 4 to 5 years.
LAb space
 The new lab space in the Sierra Hall building opened in the fall of 2015. We have 3 general labs, and 3 dedicated labs (Robotics, Embedded Systems, and Networks & Security), as well as a tutoring center. More information about our labs can be found here: http://compsci.csuci.edu/resources/labs.htm. We are also in the process of organizing further space for our Mechatronics needs, but the current labs are well set up for the initial needs.
The new lab space in the Sierra Hall building opened in the fall of 2015. We have 3 general labs, and 3 dedicated labs (Robotics, Embedded Systems, and Networks & Security), as well as a tutoring center. More information about our labs can be found here: http://compsci.csuci.edu/resources/labs.htm. We are also in the process of organizing further space for our Mechatronics needs, but the current labs are well set up for the initial needs.





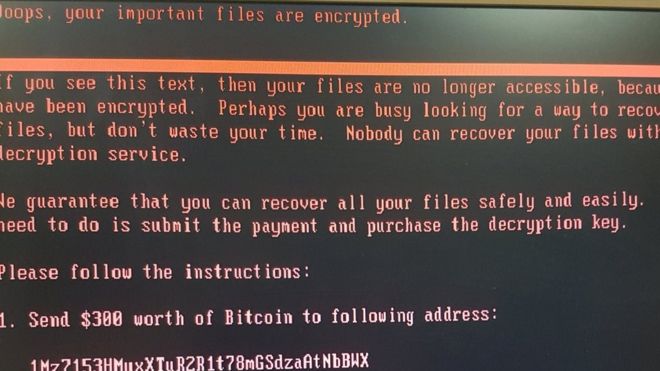 Companies across the globe are reporting that they have been struck by a major ransomware cyber-attack.British advertising agency WPP is among those to say its IT systems have been disrupted as a consequence.
Companies across the globe are reporting that they have been struck by a major ransomware cyber-attack.British advertising agency WPP is among those to say its IT systems have been disrupted as a consequence.