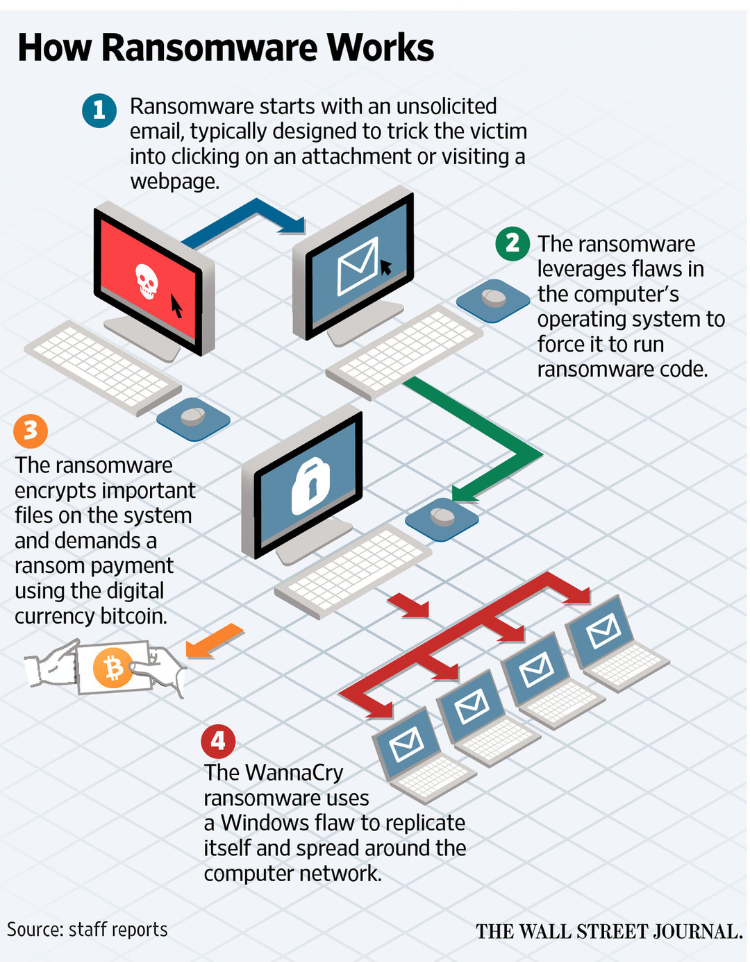
Researchers urge Windows admins to apply MS17-010 before the next attack using the EternalBlue NSA exploit deploys a worse payload than WannaCry ransomware.
No one should be letting their guard down now that the WannaCry ransomware attacks have been relatively contained. Experts intimately involved with analyzing the malware and worldwide attacks urge quite the opposite, warning today that there’s nothing stopping attackers from using the available NSA exploits to drop more destructive malware.
The key is to patch vulnerable Windows machines while there is a downtime, ensure offline backups are secure and available, and that antimalware protection is running and current.
Kaspersky Lab researcher Juan Andres Guerrero-Saade and Comae Technologies’ Matt Suiche said today during a webinar, below, that the EternalBlue exploit targeting a SMBv1 flaw could be fitted with payloads ranging from banking Trojans to wiper malware that destroys a computer’s hard disk.
“Absolutely,” Guerrero-Saade said when asked if this could have been a wiper attack rather than ransomware. “We’re talking ring0 access (via the DoublePulsar rootkitinstalled by the EternalBlue exploit). It would have just come down to a matter of implementation at that point.”
Accelerating the researchers’ anxiety about what could be next was yesterday’s ShadowBrokers announcement that it would begin in June a monthly dump of new exploits—including Windows 10 attacks—and stolen data. The ShadowBrokers’ leak in April of EternalBlue and other Windows attacks handed attackers not only the exploits but also documentation that lowered any barrier to entry for using these attacks.
“This is really worrying because we’ve seen the impact of what those files out in the wild can do,” Suiche said.
The attacks also exposed the shortcomings associated with patching, despite experts for more than a decade stressing the importance of keeping operating systems, browsers and third-party software up to date. MS17-010, the patch that addressed the SMB vulnerabilities leaked by the ShadowBrokers in April, has been available since March. Microsoft rated the security bulletin as critical and experts cautioned that this patch was to be prioritized, and that SMB port 445 on Windows machines should not be exposed to the internet. Yet, Rapid7 today said its scans have found more than 1 million internet-connected devices exposing SMB over 445 with more than 800,000 of those devices running Windows. Rapid7 said it’s likely that a large percentage of that number includes vulnerable versions of Windows with SMBv1 enabled.
“Beyond the prevalence of what these exploits might be, but it really has been a test on the industry and defenders as well,” Guerrero-Saade said. “What we saw here was not the super secret zero-day situation you can’t save yourself from. It was a test of how well we’re implementing the solutions and recommendations that have been out there a very long time that everybody touts every single day. We were asked to put our money where our mouth is with this WannaCry infection.”
The biggest mitigating factor in slowing down the WannaCry outbreak was the discovery of a so-called killswitch that was likely an evasion technique by the malware to check whether it was running in a sandbox. The malware called out to a hard-coded URL, and if it responded, the malware would not execute. The speculation is that getting a response back from the killswitch domain indicated the malware might be executing instead in a sandbox.
Researcher Marcus Hutchins of the MalwareTech blog registered the domain coded into last Friday’s version of WannaCry while Suiche registered a second and third killswitch domain found in subsequent variants, shutting down most infections in the wild.
Guerrero-Saade said his concern is that the next version likely won’t have a killswitch, and could contain a more dangerous and costly payload.
“We have essentially bought time with the killswitches. That’s something where we got incredibly lucky that was even involved in the development of the malware,” Guerrero-Saade said.
They also touched on the shared code between an early WannaCry version found in February and a sample from the Lazarus APT from February 2015. Lazarus is the North Korean group alleged to be behind the Sony hack, which featured wiper malware and damaging data leaks, as well as the SWIFT attacks against banks in Bangladesh, Poland and Mexico. The attacks against financial organizations, experts said during the Kaspersky Lab Security Analyst Summit, were performed by an internal Lazarus splinter group called Bluenoroff in an attempt to help fund the APT’s other activities.
Google’s Neel Mehta found the same code in both samples, which was confirmed by Kaspersky Lab and Suiche later. Guerrero-Saade, who worked on the Lazarus research and on separate research on APTs and their use of false flags, said today that this was not an attribution claim that Lazarus was behind WannaCry, but instead a clustering claim.
“What we’re talking about is what cluster of activity this fits into, what threat actor fits the bill for this,” he said. The linkage between the SWIFT attacks and Lazarus, made by BAE Systems researchers, was based off similar code re-use of a wiper function in a Lazarus attack and the Bangladeshi attack. “The amount of proof grew over times and we laid to rest the concerns about whether the SWIFT attackers are actually part of the Lazarus group.
“Having only had WannaCry for five days, I think it’s important to understand that this is only a lead, and not a simple lead,” Guerrero-Saade said. “It’s not necessarily easy to just replicate a very specific function of code from a very obscure piece of malware from two years ago that you only put into version 1.0 and then removed. That’s not a false flag, that’s too subtle. No one would have noticed it if not for Neel Mehta doing fantastic work.
“I understand that while it’s important to have some healthy skepticism, in this particular case, I think we’re just catching a bit of code re-use. The claims aren’t necessarily bigger than they are, but they aren’t quite as hard to stomach when you look at the code itself.”
via Next NSA Exploit Payload Could be Much Worse Than WannaCry — Threatpost | The first stop for security news



 In today’har busy world, convenience seems to outweigh consequence, especially with how people use their mobile devices. Using free public Wi-Fi networks, for example, comes with any number of serious security risks, yet surveys show that the overwhelming majority of Americans do it anyway. In a study by privatewifi.com, a whopping three-quarters of people admitted to connecting to their personal email while on public Wi-Fi.
In today’har busy world, convenience seems to outweigh consequence, especially with how people use their mobile devices. Using free public Wi-Fi networks, for example, comes with any number of serious security risks, yet surveys show that the overwhelming majority of Americans do it anyway. In a study by privatewifi.com, a whopping three-quarters of people admitted to connecting to their personal email while on public Wi-Fi.