The password challenge in COMP/IT 424, the “Security” course that I am currently teaching at Channel Islands, was to find the crypt() password corresponding to the hash:
3zLNGMUzkNwak
The winner of the challenge was Jesse Thomas, here is the password:
h7vy09s1
and here is Jesse’s approach in his own words:
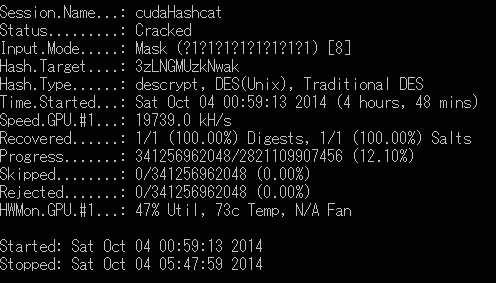
I decided to try ocl hashcat to crack the password. Since we were told that the password would be entropic, I figured we'd have to try a brute force attack. At first I was attempting to use all 94 potential characters but after seeing that it was estimated to take around 10 years to search through them all for a password length of 8 characters, I chose to search for only passwords matching lowercase characters and digits (like the previous challenge shown in class). The attempt took 4 hours and 48 minutes to complete, using a single nVidia GeForce GTX 560 Ti, which ran at a speed of 19739 kH/s (hash calculations/sec). At the time the password was cracked, hashCat had checked 341256962048 of 2821109907456 (32^8) potential combinations, so the password was found relatively early in the search algorithm (about 12% exhausted). I used this command (in Windows, where I had a stronger video card): cudaHashcat64.ex -m 1500 -a 3 -o cracked.txt "3zLNGMUzkNwak" -1 ?l?d ?1?1?1?1?1?1?1?1 -m specifies the hash type. 1500 is for descrypt/DES. -a 3 specifies a brute force attack "-1 ?l?d" specifies a custom mask with the characteristic of being lowercase and digits only "?1?1?1?1?1?1?1?1" specifies that there will be 8 characters in the password. Tried after it failed to find anything for length <= 7