On April 17, 2019, I will be speaking at the MIT Forum about Cybersecurity. This event is open to the public. For details:
Category: Cybersecurity
CI has a new student Cybersecurity club

Price of a hack podcat
Invitation to the HAAS/CSUCI Cybersecurity conference
This event is now at capacity; if you didn’t get a spot, we hope that you can join us on October 7th, for the 2nd biannual HAAS/CI Cybersecurity conference.
I would like to invite you to the first meeting of the HAAS and CSUCI Cybersecurity Conference on February 11, 2019. This is going to be a biannual conference, to be held this year at HAAS on Feb 11, and at CSUCI on Oct 7.
- Please RSVP here: https://bit.ly/2Aw4uYf
- Flyer and program
- There is no registration fee.
This conference aims to serve Ventura, Santa Barbara and LA Counties. There is a lot of interest and need in the area of cybersecurity. We have local groups that work in
- business & industry security
- Navy security
- digital forensics
- compliance, policy and law
- research & education
but it will serve all of us well to have a venue where we can all meet, learn about the latest software tools, best practices and certifications, and speak to fellow IT experts who are being proactive in defending businesses and infrastructure.
Please come and attend our first meeting at HAAS in Oxnard, and circulate this flyer among your colleagues and friends. As I said, a flyer with more information, in particular a registration email, will be circulated in January.


Microsoft Open Sources Homomorphic Encryption Library
My student Dragan Rakas and I worked on an early version of this technology in 2013, and we found it to be a very interesting but difficult problem. You can read our about it here.
 Microsoft has open sourced a homomorphic encryption library developed by its Cryptography Research group, saying it “strongly believes” the technology is ripe for use in real-world applications, as it makes the source code available on GitHub. (Here is the link to the GitHub repository.)
Microsoft has open sourced a homomorphic encryption library developed by its Cryptography Research group, saying it “strongly believes” the technology is ripe for use in real-world applications, as it makes the source code available on GitHub. (Here is the link to the GitHub repository.)
Source: Microsoft Open Sources Homomorphic Encryption Library
Great opportunity in Ventura County: DoD DRARS Cybersecurity Audit Training
Jack Goldsmith on Cybersecurity
Geetanjali Agarwal successfully defended her MSCS thesis on image recognition
My student Geetanjali (Geet) Agarwal defended her masters thesis titled Aneka – Wavelet Image Hashing Algorithm, see announcement, where the contribution is a framework of hashing algorithms for image recognition. This important work is done in collaboration with the SoCal High Technology Task Force (HTTF). Geet deployed the AWS to accomplish her results, including EC2 instances and MySQL databases used to run experiments on thousands of images. Geet’s thesis will be available after the final draft is ready.
Giving a talk on Computer Science at CI to the RDP-21 group on Nov 6 at 7:30am
On November 6, 2018, at 7:30am, I am giving a talk to the Regional Defense Partnership for the 21st Century (RDP-21) on Computer Science at CI. Here is the meeting location.
Voyager: an implementation of a tracking pixel
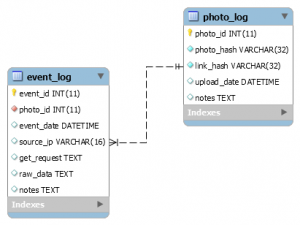 Voyager is a software that implements what is called an invisible bit (aka, a tracking bit), that can be used to track certain activities. Voyager deploys the AWS network infrastructure, and its Data Base, the Relational Database Service (RDS). Voyager has been implemented at CI by a group of Computer Science students, as a Research & Development project for the HTTF. From AWS website:
Voyager is a software that implements what is called an invisible bit (aka, a tracking bit), that can be used to track certain activities. Voyager deploys the AWS network infrastructure, and its Data Base, the Relational Database Service (RDS). Voyager has been implemented at CI by a group of Computer Science students, as a Research & Development project for the HTTF. From AWS website:
Amazon Relational Database Service (Amazon RDS) makes it easy to set up, operate, and scale a relational database in the cloud. It provides cost-efficient and resizable capacity while automating time-consuming administration tasks such as hardware provisioning, database setup, patching and backups. It frees you to focus on your applications so you can give them the fast performance, high availability, security and compatibility they need.
For this project, we are also using the following tools: EC2, S3 and Route 53.

